Zerozilla, a leading Managed SOC provider in Bangalore, India, empowers businesses to navigate the ever-evolving cybersecurity landscape. We offer comprehensive solutions like Vulnerability Assessment and Penetration Testing (VAPT) to identify and eliminate security weaknesses before attackers exploit thets. Our dedicated team also helps businesses achieve compliance with industry regulations, minimizing the risk of penalties and downtime.
Partnering with Zerozilla ensures peace of mind – you can focus on your core operations while we safeguard your data privacy, security, and intellectual property.
Network Infrastructure VAPT identifies security issues, vulnerable devices, and weak links in your network, helping detect and mitigate potential vulnerabilities.
Web application security is crucial today. Our Web Application VAPT identifies technical (OWASP Top 10 & NIST-CWE) and business logic vulnerabilities, providing detailed recommendations to enhance your security.
IT infrastructure testing, specifically Cloud Infrastructure VAPT, thoroughly examines cloud architecture to uncover potential attack vectors, from the network layer to virtual data centers.
Mobile app security ensures PCI DSS compliance via network and application layer testing. Key tools include static, dynamic, and forensic tools to identify and address risks.
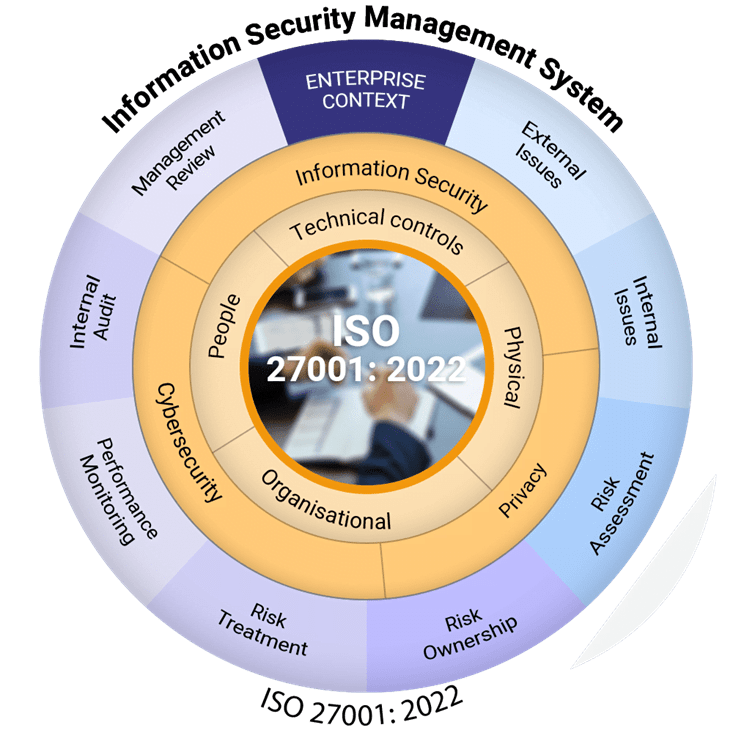


Here is a brief overview of al the phases involves in implementing ISMS-ISO 27001 certification.
Summary At this stage:
The external certification body conducts ISO 27001 certification in two phases:
After completing these phases, the certification body issues an ISO 27001 certificate. Clients are officially ISO 27001 certified upon receiving their certificates.

We engaged Zerozilla for both VAPT and ISMS services and couldn’t be more pleased with the outcomes. Their comprehensive VAPT assessments revealed critical vulnerabilities that were swiftly addressed, strengthening our defenses. Simultaneously, their guidance in implementing an ISMS provided us with a structured approach to managing our information security. The professionalism, expertise, and dedication of their team were evident throughout the engagement. Thanks to Zerozilla, we now have a resilient security framework that supports our business objectives.

Engaging with Zerozilla for our Vulnerability Assessment and Penetration Testing was one of the best decisions we made for our security posture. Their team was thorough, professional, and incredibly insightful. The detailed report they provided helped us identify critical vulnerabilities and implement effective measures to mitigate risks. Their expertise not only safeguarded our systems but also enhanced our overall security framework. We highly recommend their VAPT services to any organization serious about cybersecurity.

Our team is a diverse blend of seasoned experts and emerging talent, each bringing unique skills and perspectives to tackle cybersecurity challenges.
Our team includes certified experts who specialize in identifying and mitigating cyber threats, equipped with a deep understanding of the latest security technologies and strategies.
We develop security strategies tailored specifically to your business requirements and industry standards, ensuring a perfect fit for your security needs.
Our systems are on constant alert, scanning for vulnerabilities and ready to respond immediately to any threats, thus safeguarding your digital assets around the clock.
We provide continuous security training for your staff and offer ongoing support to enhance your organization's overall security posture, keeping you informed and prepared against potential cyber threats.
Everything you need to know about the product and billing. Can’t find the answer you’re looking for? Please chat to our team.
Zerozilla stands out thanks to our data-driven approach, experienced team, and a track record of delivering measurable results. We focus on crafting custom strategies that align with your business goals, ensuring you get the most out of your marketing budget.
Zerozilla stands out thanks to our data-driven approach, experienced team, and a track record of delivering measurable results. We focus on crafting custom strategies that align with your business goals, ensuring you get the most out of your marketing budget.
Zerozilla stands out thanks to our data-driven approach, experienced team, and a track record of delivering measurable results. We focus on crafting custom strategies that align with your business goals, ensuring you get the most out of your marketing budget.
Zerozilla stands out thanks to our data-driven approach, experienced team, and a track record of delivering measurable results. We focus on crafting custom strategies that align with your business goals, ensuring you get the most out of your marketing budget.
Zerozilla stands out thanks to our data-driven approach, experienced team, and a track record of delivering measurable results. We focus on crafting custom strategies that align with your business goals, ensuring you get the most out of your marketing budget.
Zerozilla stands out thanks to our data-driven approach, experienced team, and a track record of delivering measurable results. We focus on crafting custom strategies that align with your business goals, ensuring you get the most out of your marketing budget.
Protect your business from cyber threats with Zerozilla’s expert solutions.
WhatsApp us