



Automated scans aren’t enough. Our VAPT services (Vulnerability Assessment & Penetration Testing) employ manual exploitation techniques to find the deep logic flaws that scanners miss, ensuring your defenses are truly battle-tested.
Automated scans aren’t enough. Our VAPT services (Vulnerability Assessment & Penetration Testing) employ manual exploitation techniques to find the deep logic flaws that scanners miss, ensuring your defenses are truly battle-tested.
Tools can find 60% of bugs; we find the other 40%. Our certified experts use manual logic testing to find complex business logic errors that automated scanners can never detect.
We don't just dump a scanner report. We verify every single finding manually with a Proof of Concept (PoC), so your developers waste zero time chasing ghosts.
We don't just break it and leave. We provide developer-friendly fix recommendations and offer unlimited re-testing to ensure the patches actually work.
Our reports are designed to satisfy auditors. Whether you need VAPT for PCI-DSS, SOC 2, ISO 27001, or GDPR, our documentation meets the strictest regulatory standards.
We know how to break things without crashing them. We strictly adhere to Rules of Engagement (RoE) to ensure our testing never disrupts your live business operations.
Read how our penetration testing services exposed critical flaws in banking apps and healthcare portals before they went live.
From 10-minute manual bookings to 60-second automated workflows, discover how we helped a corporate travel desk eliminate spreadsheet chaos, slash booking errors, and achieve 2× user growth.
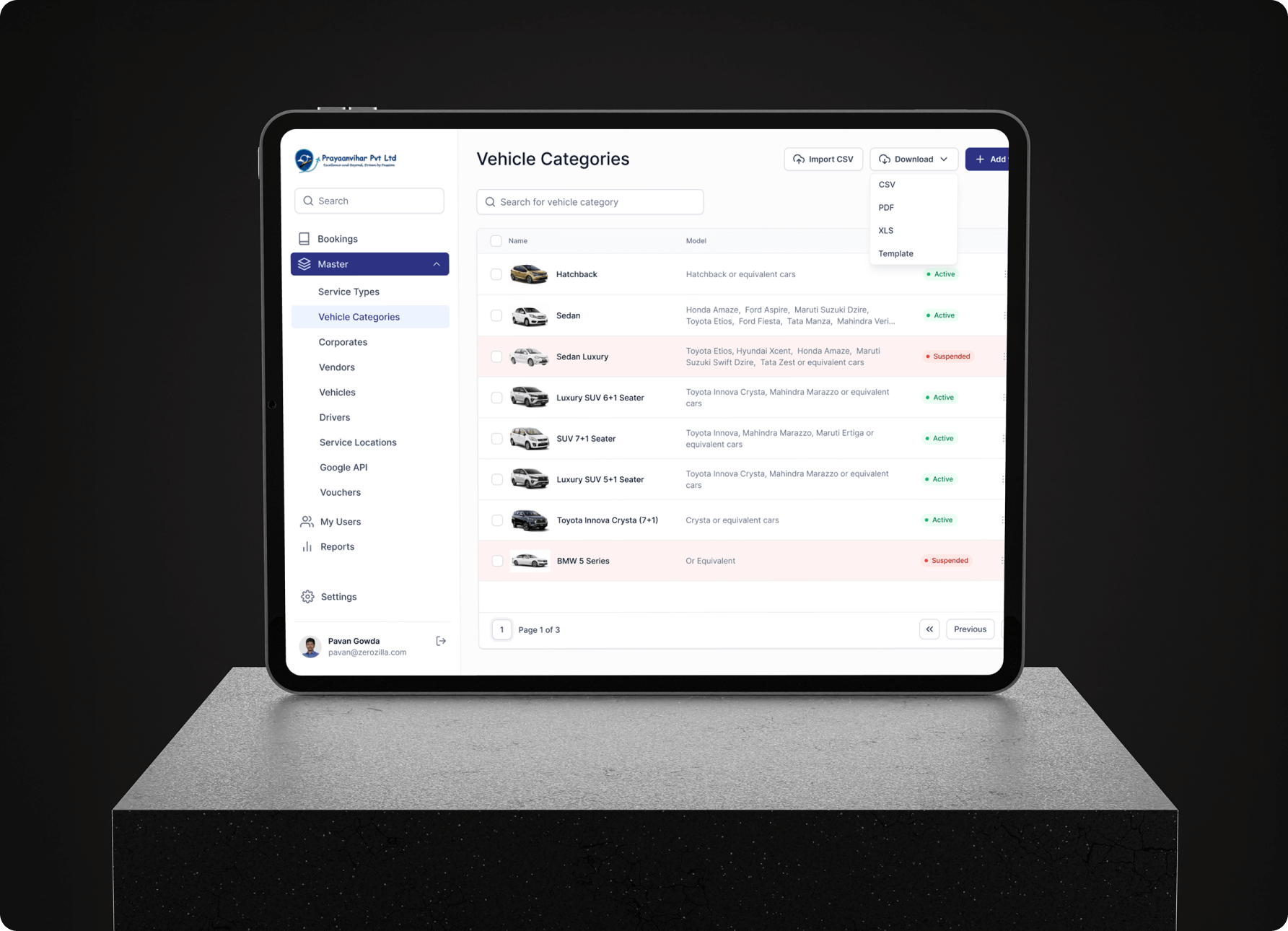
Complete operational control in one platform. 60% faster processing, claims resolved in hours, zero spreadsheet chaos. See how we unified fragmented systems with scalable infrastructure for a major optics manufacturer.

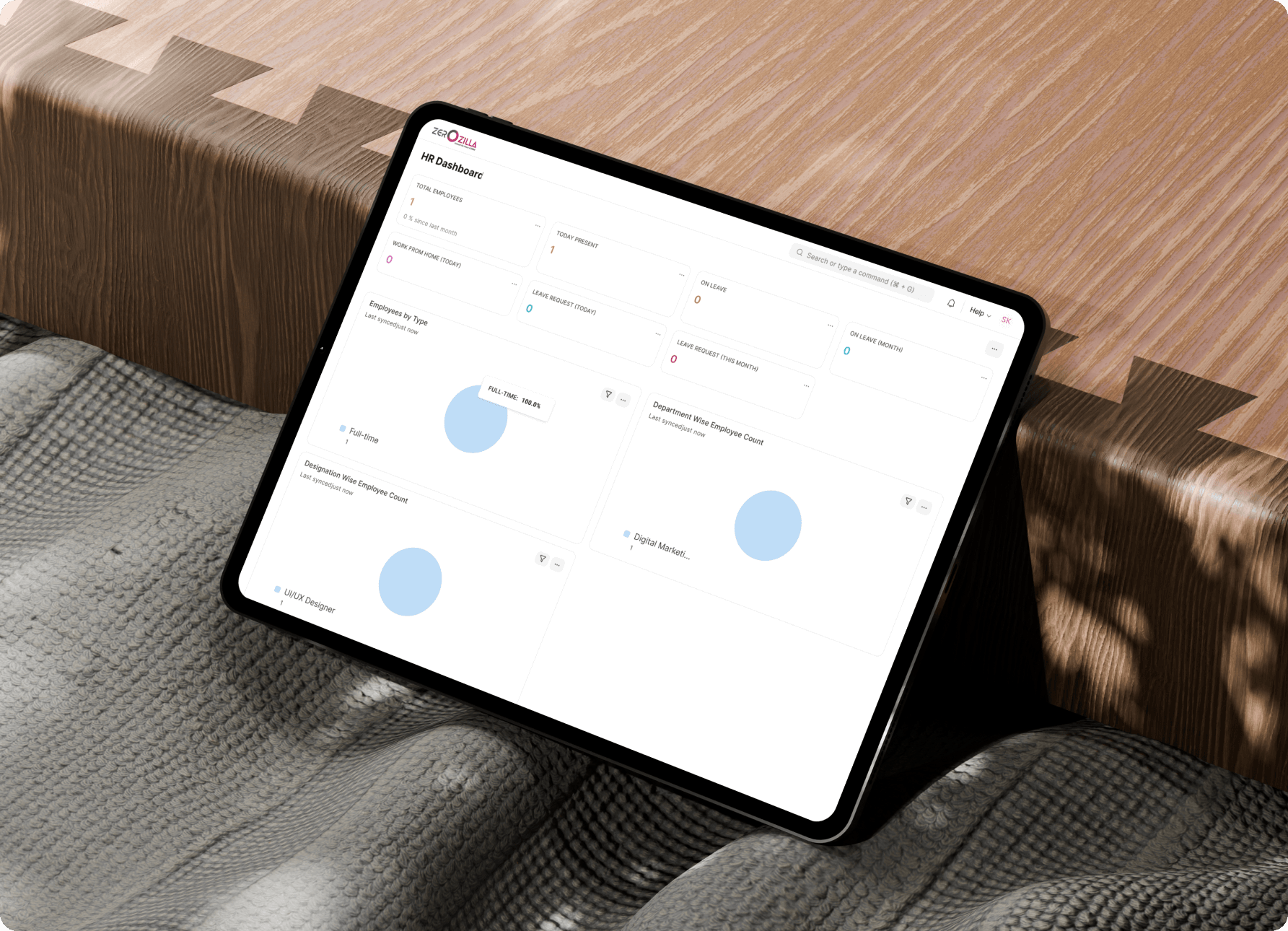
Automated HR workflows. Real-time insights. Self-service employee tools. Zero spreadsheet chaos. See how we transformed fragmented HR operations into a unified, compliance-ready system.
Our team holds the highest offensive certifications in the world, including OSCP (Offensive Security Certified Professional), OSCE, and CREST.
We write for two audiences: an Executive Summary for your CTO/Board, and a Technical Deep-Dive for your developers. Everyone gets the info they need.
We can mobilize a VAPT team within 48 hours to meet urgent launch deadlines or compliance audit requirements.

As an emerging business, Gateway sought a comprehensive solution to bolster our website, graphic design endeavors, and IT requirements. Zerozilla came highly recommended, and rightfully so. They epitomize reliability, ease of collaboration, affordability, and consistently deliver outstanding results. Without a doubt, Zerozilla is an invaluable partner for Gateway International Group, and we extend our sincere gratitude.

We have used the services of Zerozilla for building our website. The team led by Thunga and Vinay is quite responsive, flexible, creative, and methodical. They have been able to add significant value by overhauling our website and bringing it a contemporary look. The inputs particularly on improving the SEO are well appreciated.

A special thanks to our external development partner, Zerozilla, for their exceptional work in helping us go live with an upgraded landing and details page. The feature, which displays real-time return statuses, has already received glowing feedback. Zerozilla exceeded our expectations by delivering ahead of schedule with impeccable quality. This achievement highlights the power of strong partnerships and collaboration. Thank you, Zerozilla, for your stellar contribution!

Working with Zerozilla has been an absolute pleasure! Their expertise in website development truly shone through as they helped us completely revamp our online presence. The team at Zerozilla displayed a remarkable level of innovation. Communication was seamless throughout the process. The Zerozilla team’s professionalism was exemplary. Thanks to their dedication and expertise, we now have a website that reflects our work and provides visitors with a fresh perspective and an exceptional user experience.
We’ve found that the best software comes from the best partnerships. Here’s how we work with you as a trusted software development company
We gather intelligence on your assets, identifying subdomains, employee emails, and tech stacks (OSINT).
We map the attack surface to identify potential entry points and weak services.
We analyze the data to find known vulnerabilities and potential logic flaws.
The core phase. Our ethical hackers attempt to exploit vulnerabilities to gain access or escalate privileges.
We compile a comprehensive report detailing the risks, impact, and step-by-step reproduction guides.
After you patch, we re-verify the fixes and issue a "Certificate of Security" upon success.
We’ve found that the best software comes from the best partnerships. Here’s how we work with you as a trusted software development company
We gather intelligence on your assets, identifying subdomains, employee emails, and tech stacks (OSINT).
We map the attack surface to identify potential entry points and weak services.
We analyze the data to find known vulnerabilities and potential logic flaws.
The core phase. Our ethical hackers attempt to exploit vulnerabilities to gain access or escalate privileges.
We compile a comprehensive report detailing the risks, impact, and step-by-step reproduction guides.
After you patch, we re-verify the fixes and issue a "Certificate of Security" upon success.
Find quick answers to common questions about our cyber security services and delivery process

We define the assets (URLs, IPs) to be tested.
Our team attempts to breach your systems securely.
You receive a prioritized list of fixes.
No WhatsApp Number Found!
WhatsApp us